Design of a Campus Area Nework
An undergraduate project undertaken to demonstrate profieciency in Networking Fundamentals
Link to research work on google drive
Link to this research work on GitHub
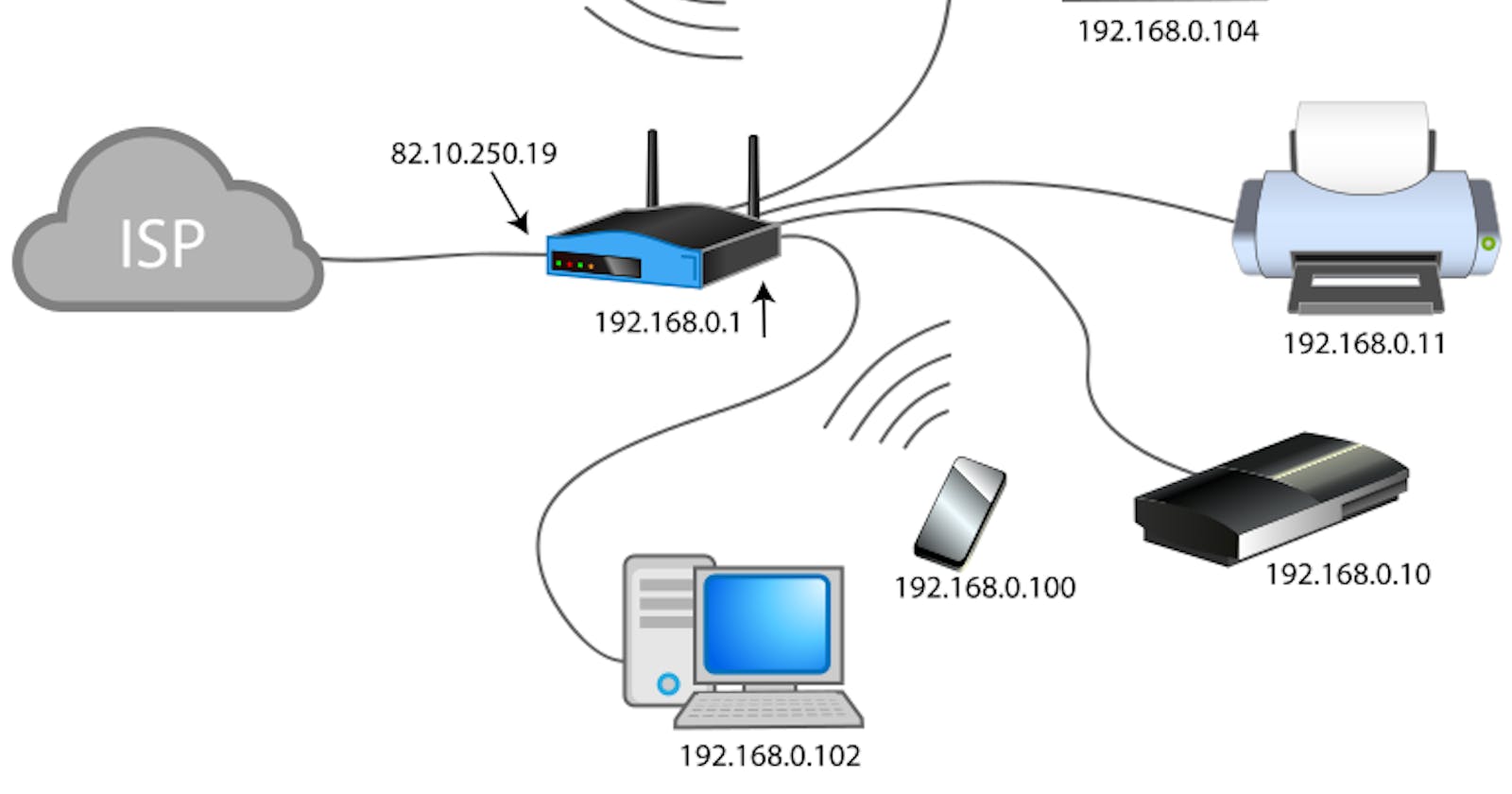
This project features a design of a campus area network for my university campus. It was undertaken by myself and my project partner. It highlights the network architecture as well as underlines the services and configurations deployed on the network to achieve seamless communication, efficient storage and systematic sharing of resources. Enumerated below is a technical breakdown of this project.
Statement of the Problem (Matters Arising)
As a student on campus for over four academic sessions, I perceived a deficiency in my school's ICT setup. The presence of a well-drilled and sustainable campus network was lacking. I believed this architecture was well long overdue and thought about how to make lecturers communicate easily, how to help admin staff easily regulate the school's activities and have managed access to data as well as give students a medium of harnessing the potential of the internet. This spur up interest within me to begin examining how computers could communicate with one another. After some research, I decided to undergo Cisco CCNA 200-301 training which highlights a whole lot that's needed to birth a career in computer networking. After successfully undergoing the Cisco training I have been able to understand and lean towards mastering computer networks. The grueling training exposed me to a host of networking fundamentals and principles. I also undertook a series of lab-based projects which helped shape my understanding and mastery of computer networks. With this knowledge, I decided to propose a logical solution to address my school's lack of a computer network. I and my project partner were able to use Cisco's packet tracer simulation application to design and configure a sustainable network architecture for the university campus.
Networking Fundamentals Employed
In the design and configuration of this architecture, we employed a lot of network principles from the Cisco 200-301 training. These basics are seen as fundamentals of every computer network. Some of the stacks covered include
IP addressing (IPV4)
Routing
Port Security
Access Control List
WAN setup
DHCP
DNS
TFTP
Network device password security
Wireless Connectivity
With this, we were able to achieve a suitable and highly scalable network design. Other stacks explored during this network design include Firewall, VPN, IPV6 addressing, VLAN, NAT and Redundancy.
Some of these policies were seen as overkill for this basic design and would rather be implemented when scaling up the network, IPV6 had no significant impact on what we planned to achieve, whereas some other policies could not be easily implemented using Cisco's packet tracer. Regardless of how the difficulties came tumbling on us, we were able to set up the network architecture.
Implementing Policies and Setting up the Network Architecture
- IP Addressing
An IP address is a unique address that identifies a device on a local network. IP addresses are the identifier that allows information to be sent between devices on a network. For this design, considering it's a campus network which has doesn't have a fixed number of working personnel, we decided to use a class B IP addressing scheme with CIDR block /20. This would ensure we would hardly ever run out of addressable IP addresses on the campus. This address range can accumulate 4094 hosts per subnet and over 65,504 network users in general. It's fair to assume this particular campus won't outgrow that number in many years to come
- Routing
Choosing a routing protocol was not so easy as there were a variety of Interior Gateway Protocols (IGP) that were suitable for our use case. Being a campus network situated in one primary physical terrain it's safe to assume the use of an IGP. Choosing a link-state IGP was best instead of a distance-based one. OSPF and IS-IS were achievable but had some limitations due to the use of the Cisco Packet tracer. We settled for the use of EIGRP because it had very fast convergence and also automatically set up backup routes. It is Cisco proprietary and also easily configurable on the packet tracer application. With the configuration of EIGRP on each router, the routers automatically set up neighboring adjacencies and can learn their routes. This makes routing over the network easy and very fast.
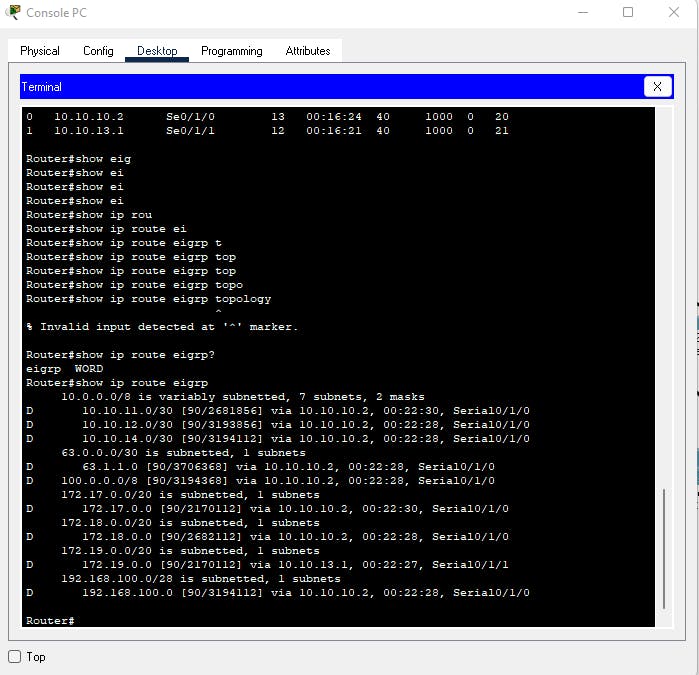
- Port Security

Port security is a security protocol that is to be implemented on switches used in a network. It safeguards against intrusion by unwanted personnel. The network admin can set up port security in two ways. One of which is to manually assign mac addresses to ports or to use sticky addresses in which the switch learns the mac addresses that come in and gets bound to it. Port security can be set to either protect, restrict or shut down. We set port security to shut down. This will automatically shut down the link thereby halting access by an unknown or unauthorized user.
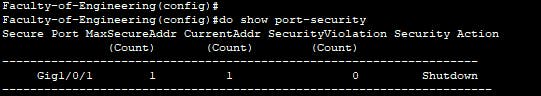
- Access Control List
Access Control List is a feature used to filter traffic to certain networks. An access control list can deny or permit a user or group of users access to some network resources. Access Control List could be standard or excluded. A standard access list could filter traffic based on IP protocols whereas, extended as the name implies could filter traffic access based on IP, TCP or even UDP protocols. We simply want to restrict access to the admin block network so that only admins on the faculty networks could have access to the admin block. So we configure a standard access list and permit only the necessary admins and deny traffic from all other network users. This way only vetted communication can come into the admin block which has a high-security tolerance
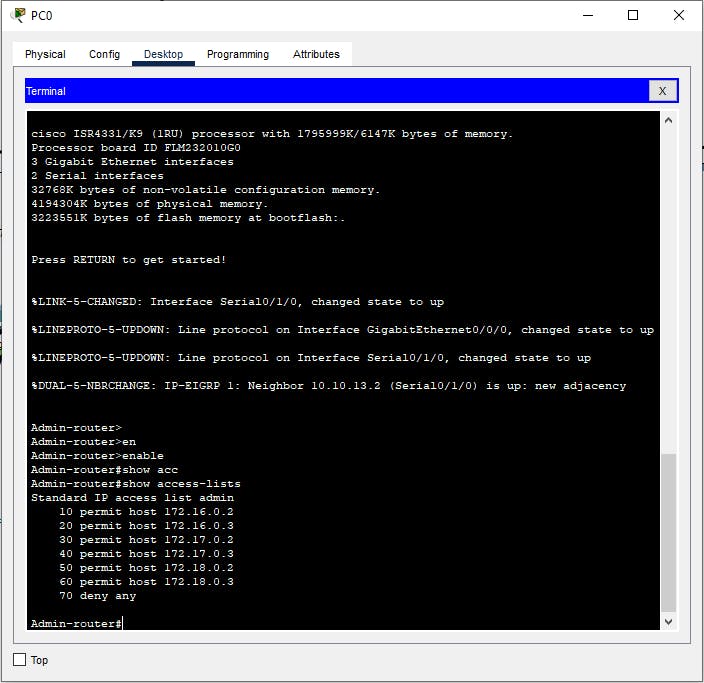
- WAN Setup
WAN technology is a way of extending a LAN over a certain geographical terrain. In our use case, a WAN connection is used to depict the provision of high-speed broadband internet by a dedicated Internet Service Provider. WAN technology could come in via DSL, leased lines, fiber connection or even wirelessly. In our case, a fiber connection will be run by the ISP to provide high-speed internet to power innovation on the campus

- DHCP
Dynamic Host Configuration Protocol (DHCP) is a protocol that aids in automatically assigning IP addresses to network users. The manual assignment of IP addresses can sometimes become very cumbersome and tedious especially when the network is large. To this effect, a DHCP server can be set up to dispense available IP addresses from a DHCP pool. In our use case, the DHCP will be very effective in assigning IP addresses to wireless devices on the network. No matter the position of the wireless device, it will be apportioned an Ip address immediately after it hooks up to one of the WIFI Access Points (AP)
- DNS
Domain Name System (DNS) is a name resolution service that allows the mapping of real-world hostnames to IP addresses. It will be worrisome if we had to memorize every user's IP address before we could establish communication with them. DNS gives us the privilege of being able to assign a hostname to all devices on the wired network. This makes communication more easy and adaptable for human
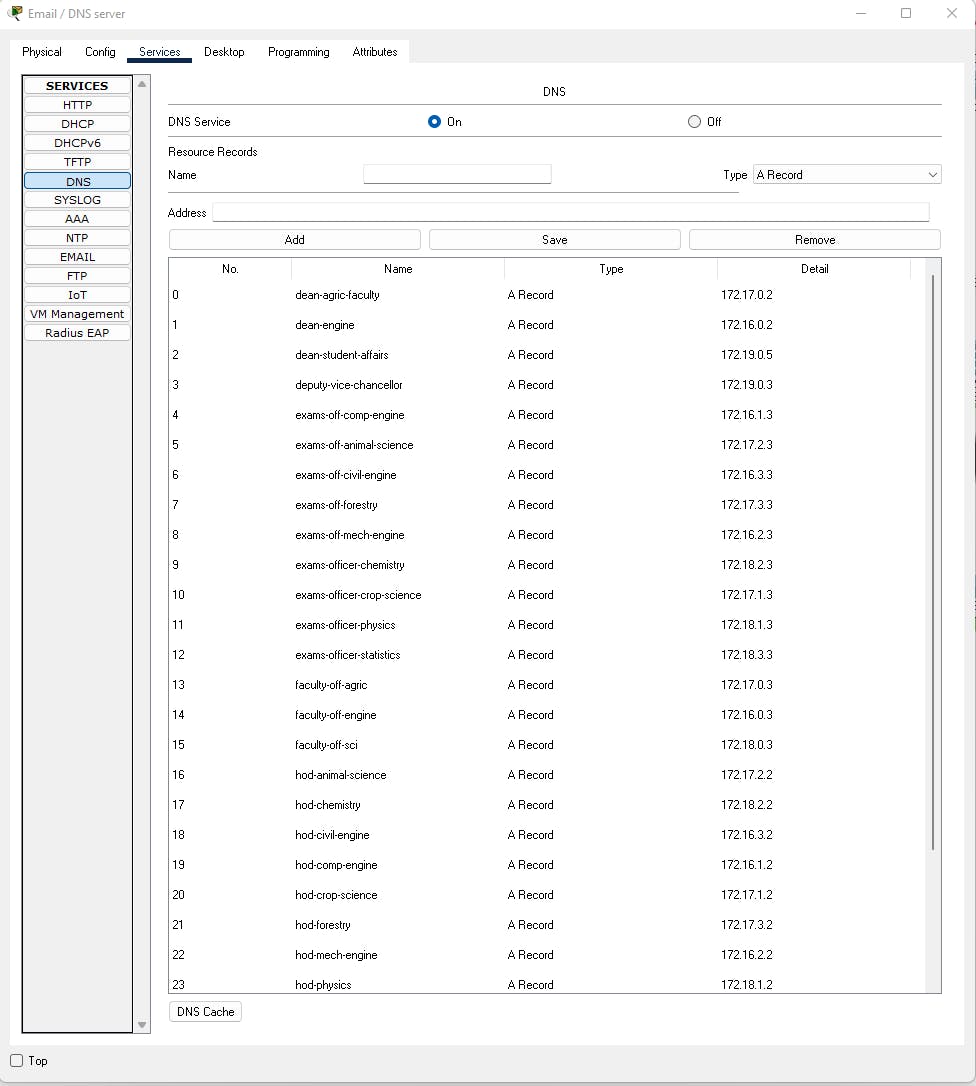
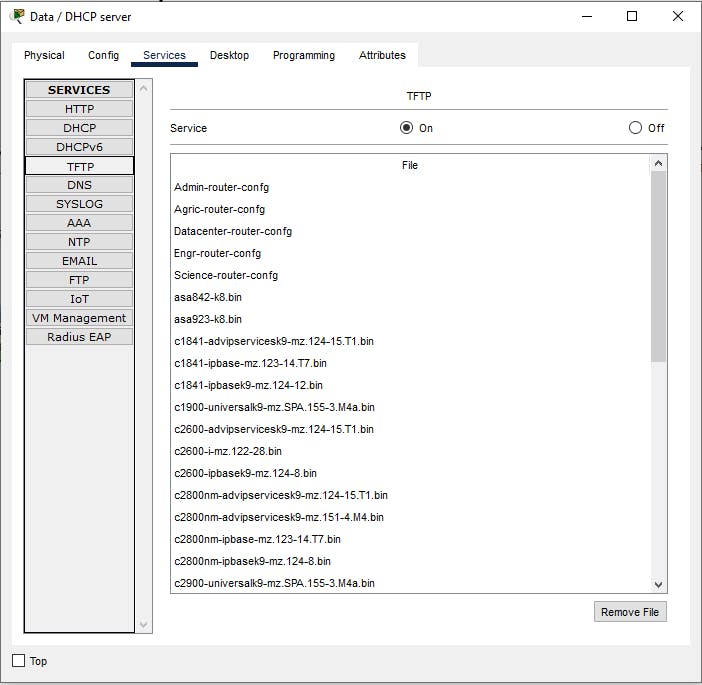
- TFTP
Trivial File Transfer Protocol is a simple secured protocol for exchanging files between two devices communicating over TCP/IP. TFTP servers allow connections from a TFTP Client for sending and receiving files. TFTP protocol supports only file send and receive operations. In this network design TFTP will be used to store and also retrieve data from the server. Its simplicity makes it very fast in data exchange. This will also see TFTP being used to back up the router configurations to the central data server so that they can be easily retrieved in case there is a sudden crash in the router's configuration.
- Network device password security
Security in any network entails a bunch of practices aimed at toughening the network to forestall any sudden attack or offensive onslaught by nefarious personnel. Passwords have been one way of preventing unauthorized access in all fields of life. In this architecture, we would set up more than one password to help guard against unwanted access. A Line console password will be set to safeguard against unwanted connection to the router using the console port. A VTY password will be set to prevent access via a remote connection such as telnet or ssh. An enable password will be set to ensure that only authorized personnel have access to the router's privilege mode. All these passwords will help boost the integrity of the network.
(PS:) For ease of access to this work, we have disabled all the passwords set on the routers. For your use case kindly set the passwords yourself
- Wireless Connectivity
A wireless network extends a wired network. A wireless network allows devices to stay connected to the network but roams untethered to any wires. Access points amplify Wi-Fi signals, so a device can be far from a router but still be connected to the network. With wireless networks comes mobility, expandability and beefed-up security. In our proposed design, the wireless network is the core fulcrum used to extend internet connectivity to all users on the campus. Anyone on campus can easily hook up. Wireless users will be restricted from having access to users on the wired network. The wireless network will be in VLANs and separated from the wired. This will help maintain the integrity and sanity of the core staff who are on the wired network and will also help keep the network resources from getting easily flooded.
Future Projections
As tech trends globally continue to emerge to simplify human lifestyles, more robust ways of going about networks keep springing up. The term Software Defined Networking (SDN) highlights an approach to networking that uses software-based controllers or application programming interfaces (APIs) to communicate with underlying hardware infrastructure and direct traffic on a network. This model differs from that of traditional networks, which use dedicated hardware devices (i.e., routers and switches) to control network traffic. SDN can create and control a virtual network – or control traditional hardware – via software.
It will continually be in our intentions to remodel this design using SDN. With SDN we will be able to have improved flexibility, a robust and secure network as well as a customizable network infrastructure.
Conclusion
This network model is basic and open to modifications to make it deployable at an enterprise-grade level. All forms of suggestions and modifications are welcomed. The packet tracer file is open and can be easily downloaded and modified. Modifications or new inclusions can be submitted as commits. I'm buzzing to see how far we can grow and advance this model.
Gracias 🙏